Install Env Via Tencent Marketplace
Refer to Overview▸, using AutoMQ Cloud requires environment setup first. This article introduces how to install the BYOC environment from Tencent Cloud applications.
The terms AutoMQ Product Service Provider, AutoMQ Service Provider, and AutoMQ mentioned in this article specifically refer to AutoMQ HK Limited and its subsidiaries.
Operation Process
Step 1: Prepare VPC and Operate Cloud Account
The AutoMQ BYOC environment is deployed within the user's VPC to ensure data privacy and security. Before installing the AutoMQ environment, a usable VPC must be prepared. The VPC must meet the following requirements:
Subnet CIDR Requirements: The AutoMQ data plane cluster is deployed within the user's VPC and will consume IPs from the VPC subnet. It is recommended to allocate sufficient available IPs under each subnet (suggested no fewer than 1,000 available IPs per subnet) to avoid issues with subsequent cluster deployment and expansion.
Public network access requirements: Deploying the AutoMQ data plane cluster requires pulling Docker images and Helm Chart artifacts from the public network. Therefore, the VPC environment needs to support public network access through SNAT or similar methods. For instructions on configuring public SNAT, please refer to the appendix of this document Install Env via Tencent Marketplace▸.
To install the BYOC environment from Tencent Cloud applications, the cloud account to be operated must be the main account or a CAM sub-account with the relevant permissions granted. If the current operation on the Tencent Console uses a CAM sub-account, the following operation permissions need to be granted before proceeding with the service activation.
- QcloudCloudappInstallationAccess: Access Tencent Cloud application products and execute application installation operation permissions.
Step 2: Install AutoMQ from Tencent Cloud Marketplace
- Visit the AutoMQ application link. The AutoMQ Cloud BYOC environment is distributed through the cloud application by default on Tencent Cloud, and users can subscribe to AutoMQ from the Cloud Application.
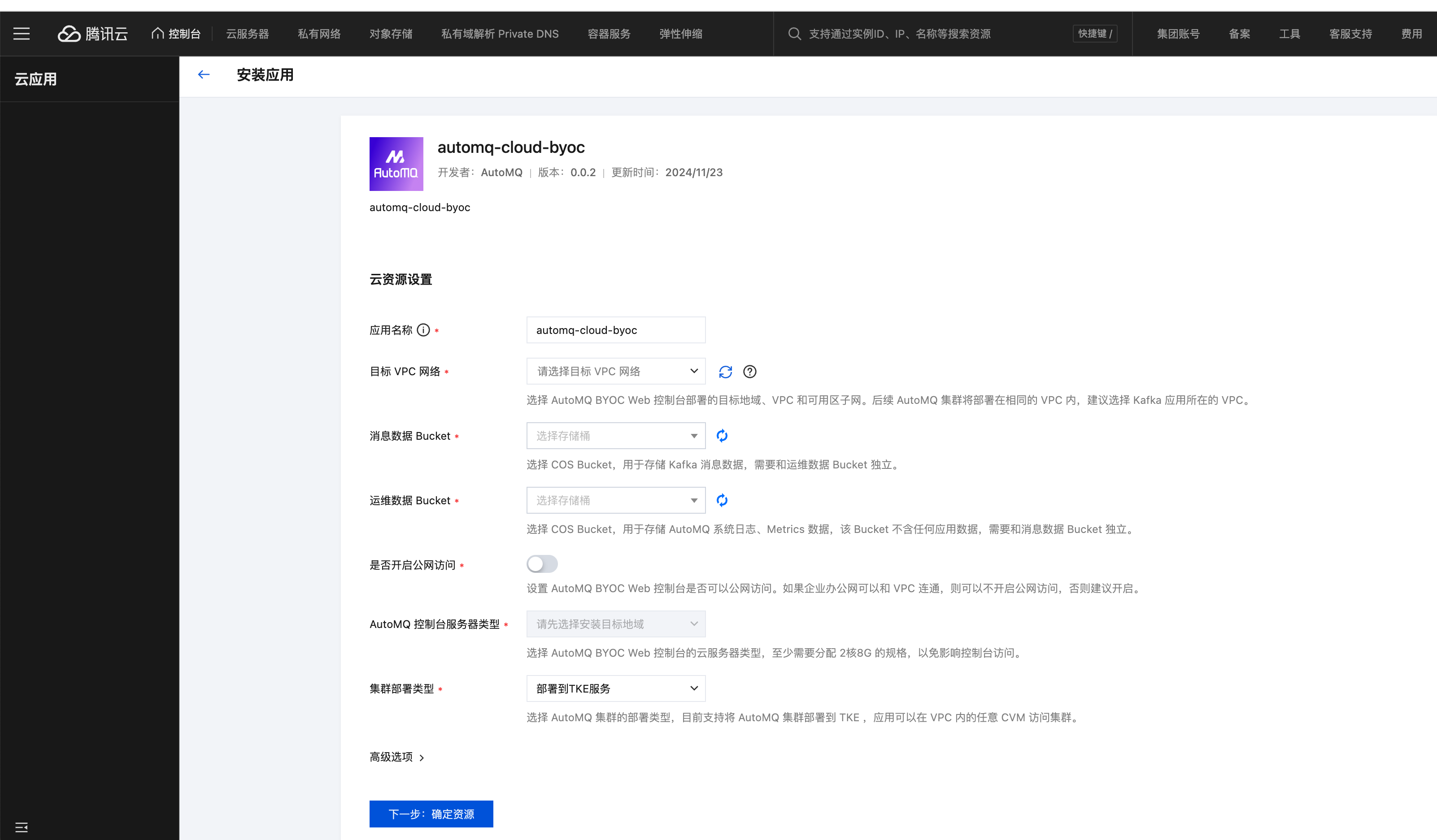
- Set the required parameters and click Confirm Resources.
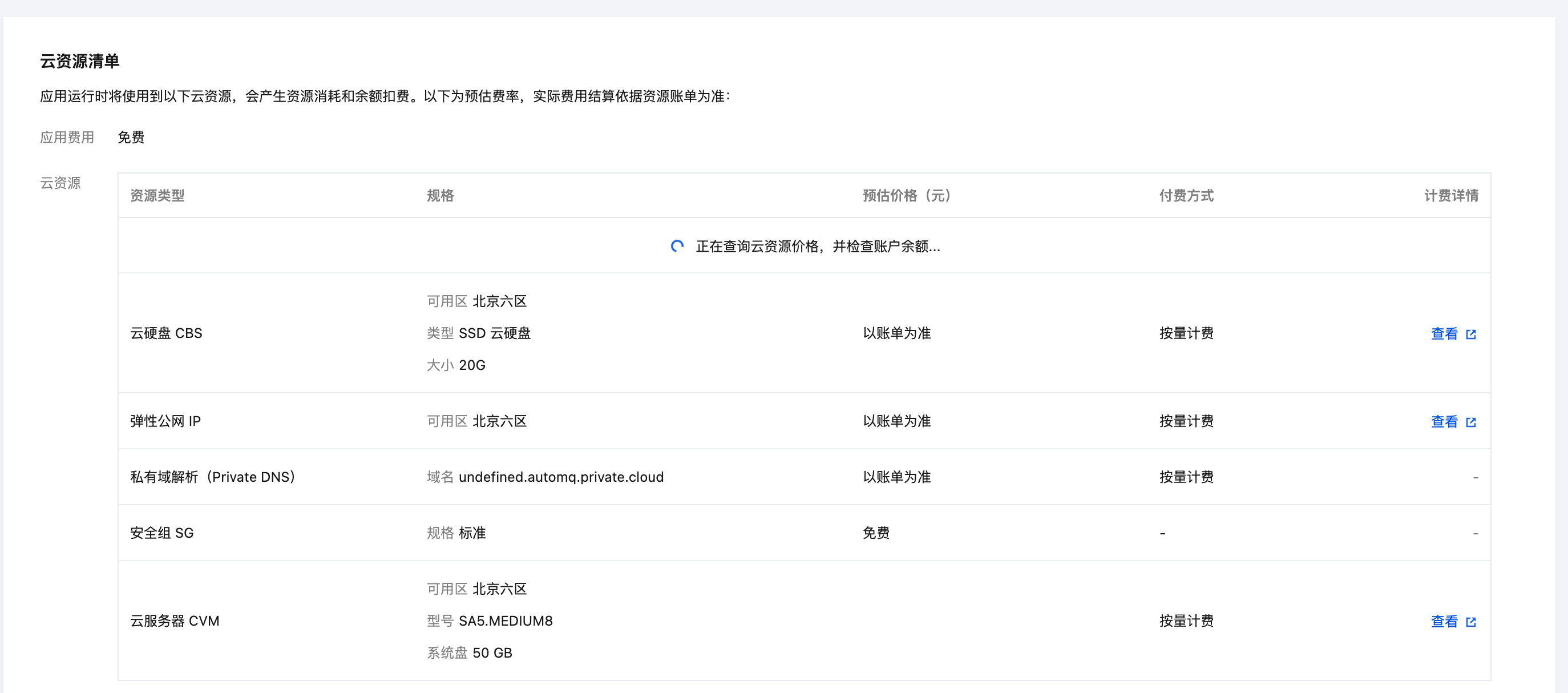
- After the installation is complete, check the application details and enter the environment console.
- View the initial account password and console address output by the cloud application console.
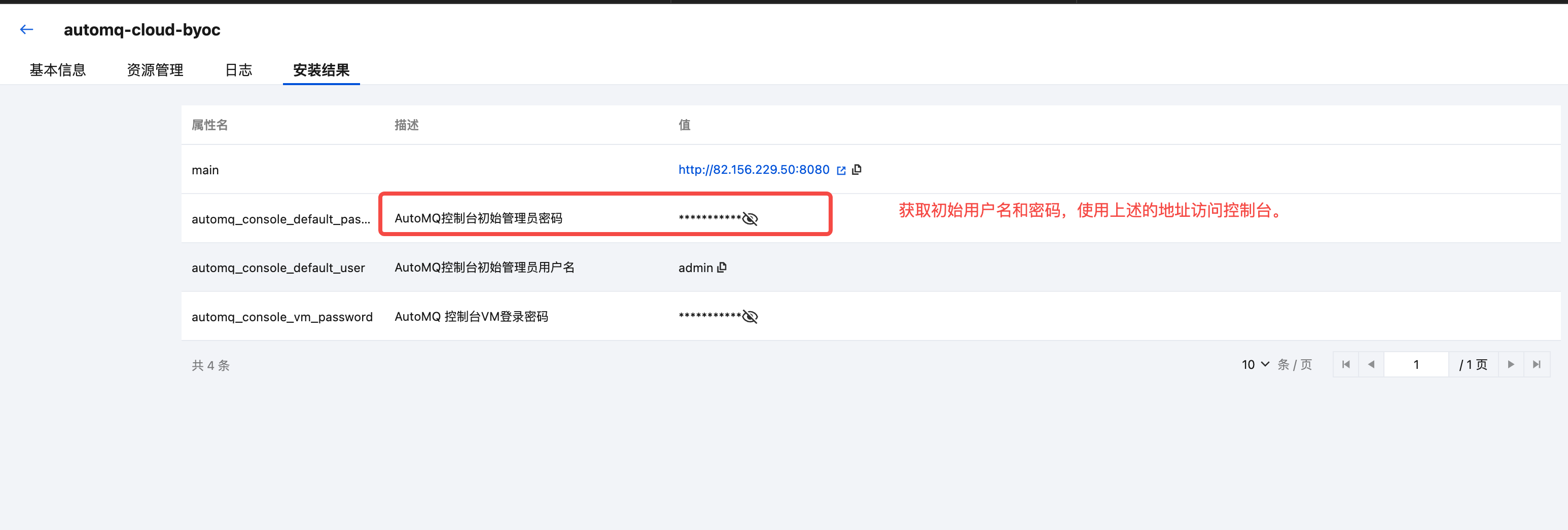
- Use the above information to log in to the AutoMQ console.
Step 3: Complete BYOC Environment Operations Authorization
The BYOC environment is deployed in the user's VPC, providing data security and privacy isolation. However, system logs, metrics, and other non-business-related system data will be generated within the BYOC environment. After the environment installation is completed, users need to refer to Manage Environment Ops Authing▸ to provide the AutoMQ service provider with the necessary operations authorization to facilitate system stability monitoring and fault self-healing operations.
Next Steps
Currently, AutoMQ on Tencent Cloud only supports deployment to TKE clusters. Therefore, after completing the environment installation, users need to prepare a TKE cluster, then configure it in the AutoMQ console and deploy the AutoMQ cluster to TKE.
For documentation on preparing TKE and completing subsequent deployment, please refer to Deploy to Tencent Cloud TKE▸.
Appendix
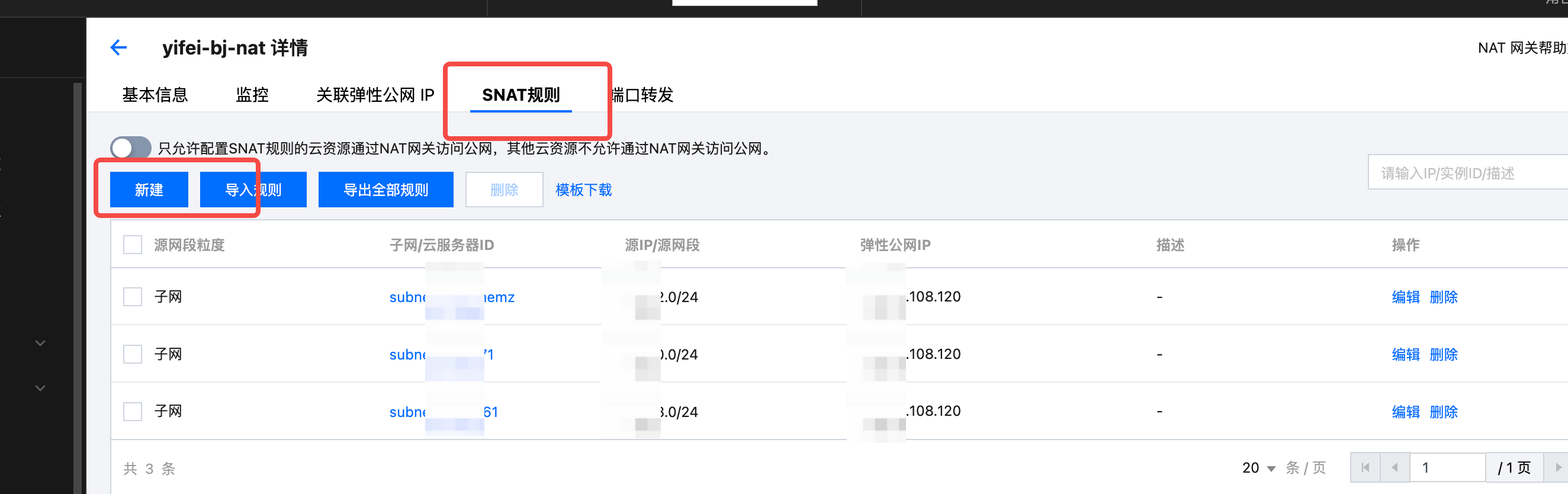
VPC Public SNAT Operation Instructions
The deployment chart and Docker image repository of AutoMQ on Kubernetes are public addresses. Therefore, when pulling images within the Tencent Cloud TKE cluster, you need to ensure that the current VPC subnet has the ability to access public addresses.
It is generally recommended to configure a public NAT gateway to achieve outbound internet access. Refer to the following steps for the operation instructions:
- Create a NAT Gateway: Go to the NAT Console to create a public NAT gateway.
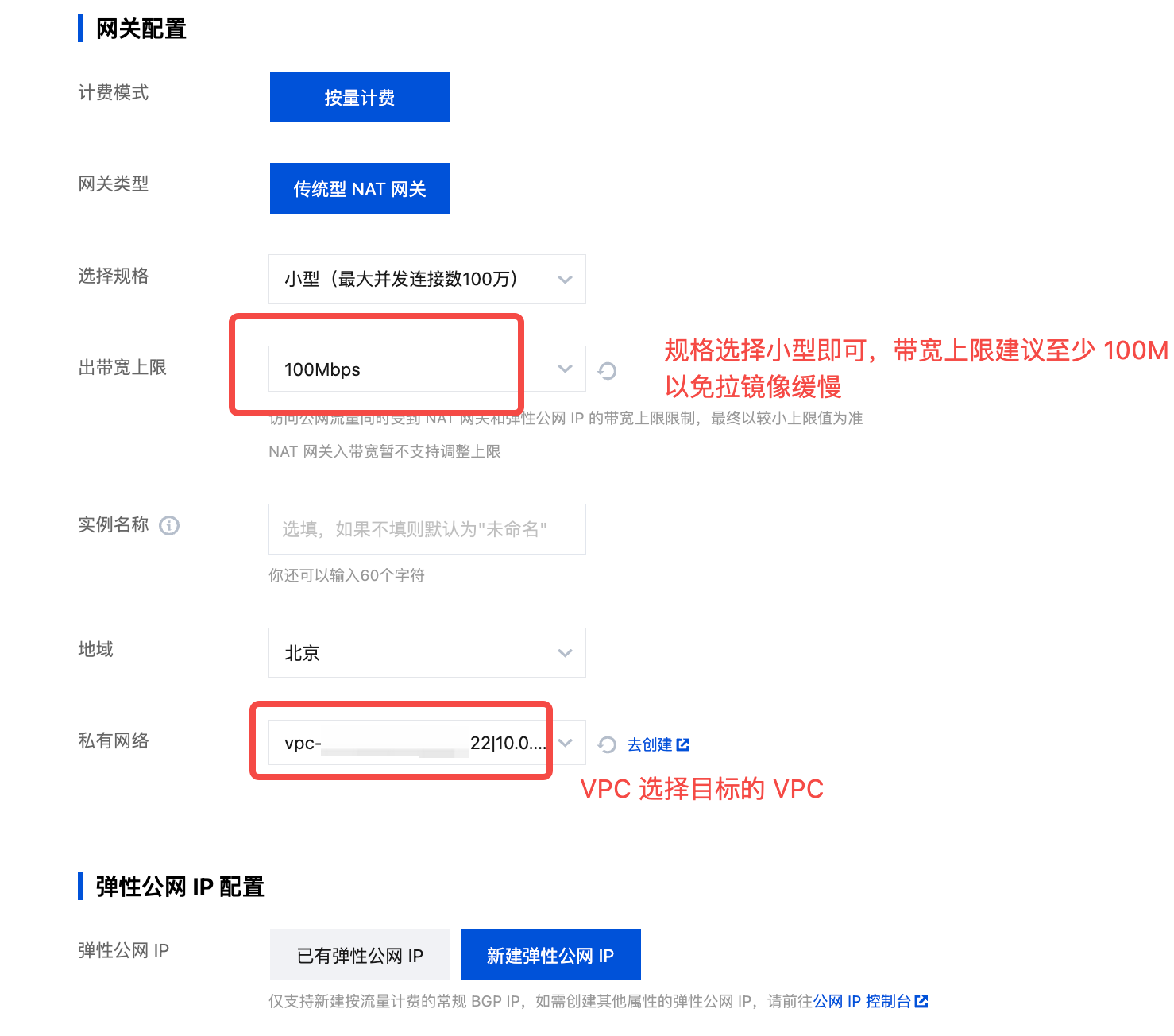
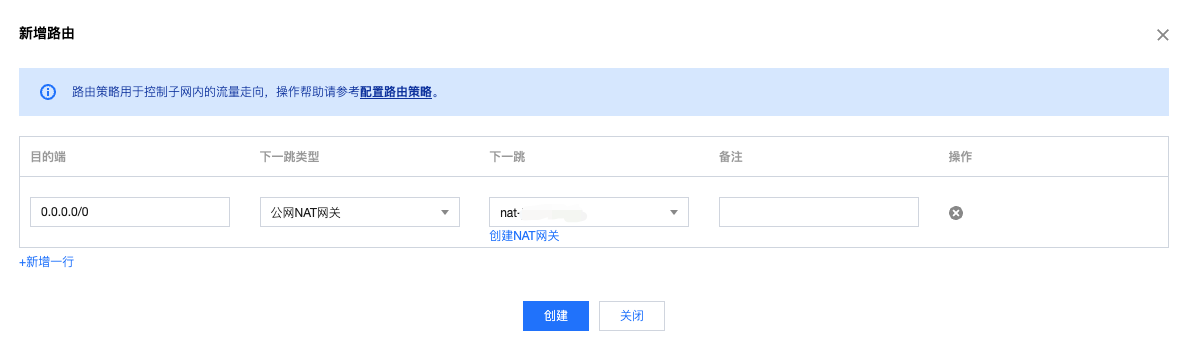
- Locate the target VPC and subnet, and add the associated route for the NAT gateway.
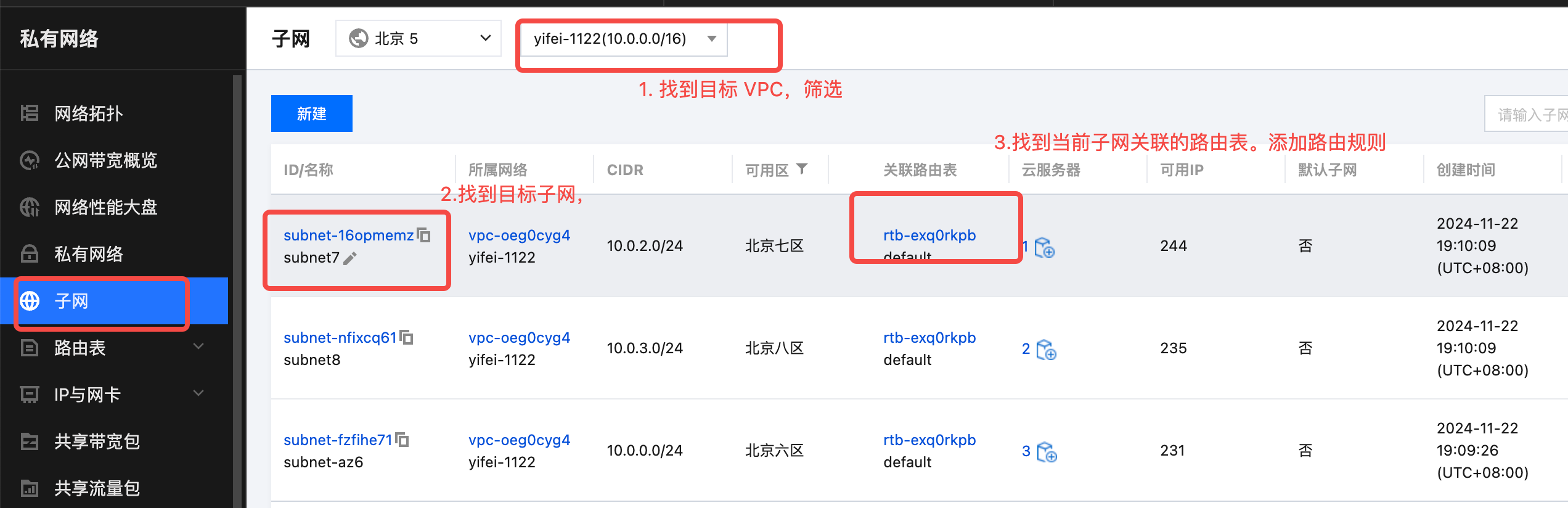
Set the target subnet, specify the next hop as the public NAT, and set the NAT gateway created in the previous step.
- Go to the NAT gateway, create an SNAT rule, and associate it with the subnet that needs public access.