Account Types
AutoMQ Cloud offers two types of accounts: Member Account and Service Account. Their definitions and differences are as follows:| Account Type | Roles and Differences |
|---|---|
| Member Account |
|
| Service Account |
|
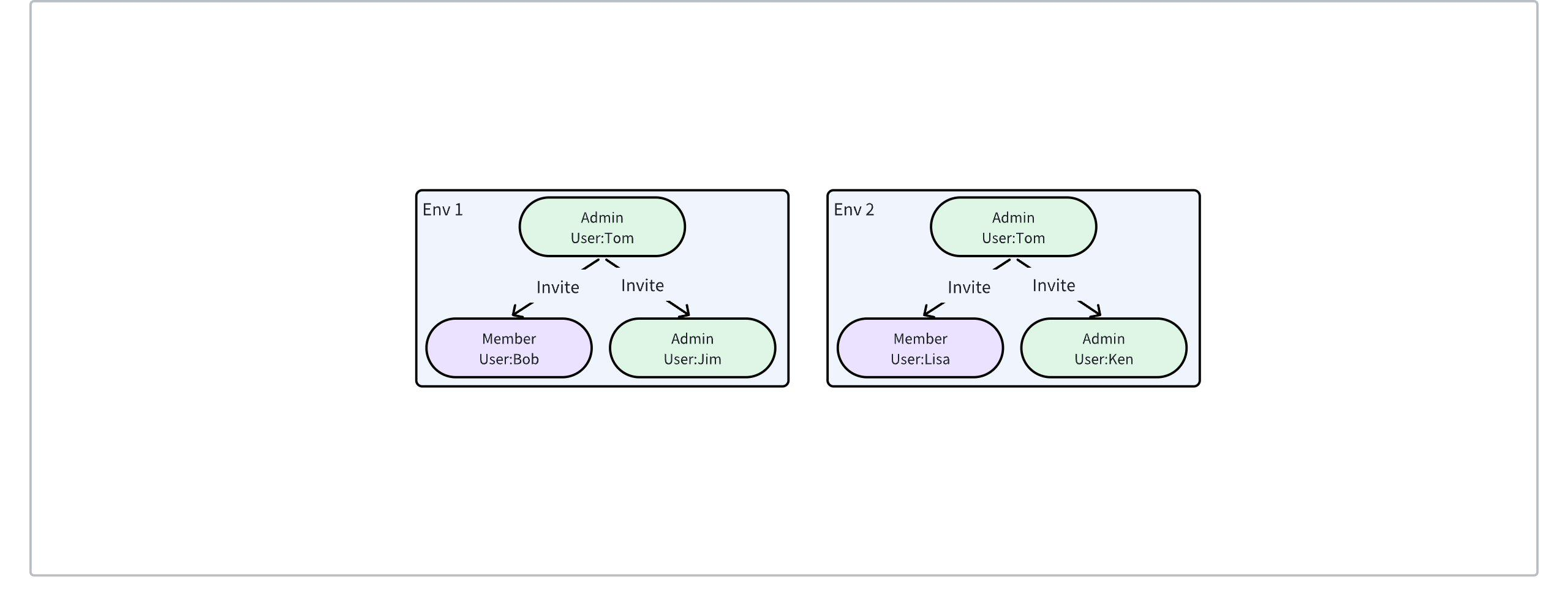
Member Account
Definition
Member accounts are system-generated by default, manually created by existing environment members, or automatically created through enterprise SSO login, serving as credentials for environment-level operations. Member accounts support multiple roles based on the required permission scope, currently including Admin, Operator, and Viewer roles.Creation Method
- Local Type: The initial Admin member of each environment is automatically created by the system upon environment creation. Subsequent members can be manually created by Admin members.
- SSO Type: AutoMQ supports configuring enterprise Identity Provider (IDP) services. Environment members of the SSO type are created through SSO login.
Relationship Between Environment and Environment Members
When a new environment is created, the system will automatically initialize and create an Admin role member for the current environment. Subsequent members are then created by the initial Admin member.